Continued from Part 3
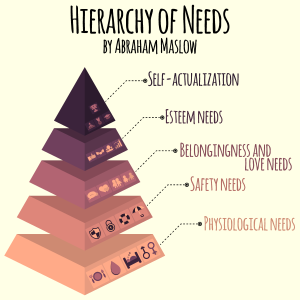
Now that we know we need a method, some philosophical handbook to help us negotiate the tumultuous sea of security and access control products beyond computational benchmarks, Maslow’s sundial for the infinitely complex foundation of human needs can do just that. It is a way of calculating how far a product or service truly goes in offering the full range of what you might want, one that is more qualitative than just mathematical. Maslow’s ‘pyramid’ doesn’t have to be an absolute checklist of necessities, either. Instead it will allow better decision making that can take into account the full range of competing and conflicting values that go into any organization. It does this by weighing the strength and weaknesses of one’s overall security approach. Let’s first outline the specifics of this framework as it relates to the context of access control and security technologies.
Step 1 – Basic Security Needs
The first rung of the ladder is the physiological, or better thought of as the ‘basic security needs.’ This makes your first, and perhaps most important, step to figure out what your physical security needs are in terms of building access, threat management, “incident response programs,” or other forms of security controls.[1] Physical security can include everything from the classic ‘bank safe,’ door locks, or hallway lockers, all the way up to entrances with iris-scanning biometric technology, 3D-capable facial recognition sensors, or smart storage that is accessed via mobile credentials. The common denominator, however, is that physically-interactive level, the places people pass through and the assets that need secured, as well as any basic threats to one’s physical well-being.[2]
In the realm of cybersecurity many have noted the need for greater synergy between the network, all of the devices connected to them, and isolated forms of security used to defend them. For example, Sleiman calls for a, “new paradigm [of] ‘next level networking.’” In it, technology and data management are core tenants to any security package.[3] As our lives have become increasingly digital, so too have our basic security needs. Other have also found that a more robust cybersecurity plan further reinforces physical security. This convergence will only become more important as our cities become smarter and our devices more interconnected.[4]
As discussed earlier, this is the level where much of the discourse on comparing access control and security technologies resides. The features and statistics surrounding different metrics are valuable, but it is also equally important to be cognizant of the purpose that they ultimately serve, that of physical security. This is a critical step in the process, but it is not the only consideration when finding the right solution for one’s organization. The next steps become a means of selecting those other priorities, filtering them through other concerns, such as budget, and finding the correct fit for a unique situation.
Step 2 – Safety, Where Security Meets Peace of Mind
As we ascend to the second tier of Maslow’s pyramid, we see that our ‘basic security needs’ have not gone away but become more nuanced. Here, safety is more than just physical threats, it asks that security is buttressed with the kind of systems and technologies that combine to create a safe, warm atmosphere with it. Let us take the example of a maximum security prison. A space can be locked down to provide for ultimate security, you can put bars on all of the windows and entrance points, armed personnel can swoop in to eliminate any potential threats, and, due to a challenge like COVID-19, you can add biological hygiene to the requirements so that your prison is hospital-clean. However, unless your space is actually a prison, it will not be the most inviting environment.
Safety reminds you that security cannot come at the expense of peace of mind. It is a means to soften your security approach, adding other values to the mix by working in concerns that already exist, such as hygiene, privacy or even something like ensuring effective economic transactions. This level can actually be a good case study for the use of Maslow’s Hierarchy, as certain technologies previously deemed primarily as accessories of convenience, such as ‘contactless access control’ and ‘contactless payments,’ which would have been located farther up the pyramid in the past are now needing to be addressed earlier, seen as integral to any basic safety plan. This also includes redesigning spaces to allow for social distancing, or the range of safety measures that might not provide absolute security, but aid in the overall peace of mind when that goal cannot be achieved, such as temperature monitoring stations or cameras, and managing large group interactions through live data analysis. Instead of constructing the perfect prison, safety demands that our security also speaks to the other important values of a functioning organization. The following levels only adds further depth to those values, teasing out the conditions that will foster growth as opposed to hindering it.
Continued in Part 5
Endnotes
[1] Crandall, Carolyn. “Measuring the Effectiveness of Your Security Controls.” Attivo Networks. March 6, 2017. https://attivonetworks.com/measuring-effectiveness-security-controls/ (accessed June 22, 2020).
[2] Banks, Martin. “How Technology is Helping Our Security.” Techaeris. May 20, 2020. https://techaeris.com/2020/05/20/how-technology-is-helping-our-security/ (accessed June 3, 2020).
[3] Sleiman, Cherif. “Security in the Age of Digital Transformation.” AME Info. June 3, 2020. https://www.ameinfo.com/industry/technology/security-in-the-age-of-digital-transformation (accessed June 3, 2020).
[4] Orme, David. “Biometric Identity: the Key to Security for Smart Cities.” IT ProPortal. June 8, 2020. https://www.itproportal.com/features/biometric-identity-the-key-to-security-for-smart-cities/ (accessed June 10, 2020).